It is impossible to imagine modern computer technologies without combining all kinds of devices in the form of stationary terminals, laptops, or even mobile devices into a single network. Such an organization allows not only to quickly exchange data between different devices, but also to use the computing capabilities of all units of equipment connected to the same network, not to mention the possibility of access to peripheral components like printers, scanners, etc. But by what principles is this done Union? To understand them, it is necessary to consider the structural diagram of the local network, often called the topology, which will be discussed further. Today, there are several main classifications and types of combination of any devices that support network technologies into one network. Of course, we are talking about those devices on which special wired or wireless network adapters and modules are installed.
Schemes of local computer networks: the main classification
First of all, in considering any type of organization of computer networks, it is necessary to build on exclusively the way computers are combined into a single whole. Here we can distinguish two main areas used in creating a local network scheme. A network connection can be either wired or wireless.
In the first case, special coaxial cables or twisted pairs are used. This technology is called an Ethernet connection. However, if coaxial cables are used in the local area network circuit, their maximum length is about 185-500 m at a data transfer rate of no more than 10 Mbps. If twisted pairs of classes 7, 6 and 5e are used, their length can be 30-100 m, and the throughput ranges from 10-1024 Mbit / s.
The wireless scheme for connecting computers on a local network is based on the transmission of information via a radio signal, which is distributed between all connected devices that distribute devices, which can be routers (routers and modems), access points (ordinary computers, laptops, smartphones, tablets), switching devices (switches, hubs), signal repeaters (repeaters), etc. With this organization, fiber optic cables are used that are connected directly to the main distributor cash equipment. In turn, the distance over which information can be transmitted increases to about 2 km, and in the radio frequency range, the frequencies 2.4 and 5.1 MHz are mainly used (IEEE 802.11 technology, better known as Wi-Fi).
Wired networks are considered to be more protected from external influences, since it is not always possible to directly access all terminals. Wireless structures in this regard lose quite a lot, because if desired, a competent attacker can easily calculate the network password, gain access to the same router, and through it get to any device that is currently using the Wi-Fi signal. And very often it is strictly forbidden to use wireless equipment in the same state structures or in defense enterprises of many countries.
Classification of networks by the type of connection between devices
Separately, we can distinguish the fully connected topology of computer connection schemes in the local network. Such an organization of connection implies only that absolutely all the terminals included in the network are connected to each other. And as already clear, such a structure is practically unprotected in terms of external intrusion or when intruders penetrate the network through special virus worms or spyware applets that could initially be written on removable media that the same inexperienced employees of enterprises could unknowingly connect to your computers.
That is why other connection schemes in the local network are most often used. One of these can be called a cellular structure from which certain initial bonds were removed.
General scheme of connecting computers on a local network: the concept of the main types of topology
Now briefly dwell on wired networks. In them, you can apply some of the most common types of building local area network schemes. The most basic types are star, bus, and ring structures. True, it was the first type and its derivatives that received the most application, but it is often possible to find mixed types of networks, where combinations of all three main structures are used.
Star Topology: Pros and Cons
The local network scheme "star" is considered the most common and widely used in practice, when it comes to using the main types of connection, so to speak, in its purest form.
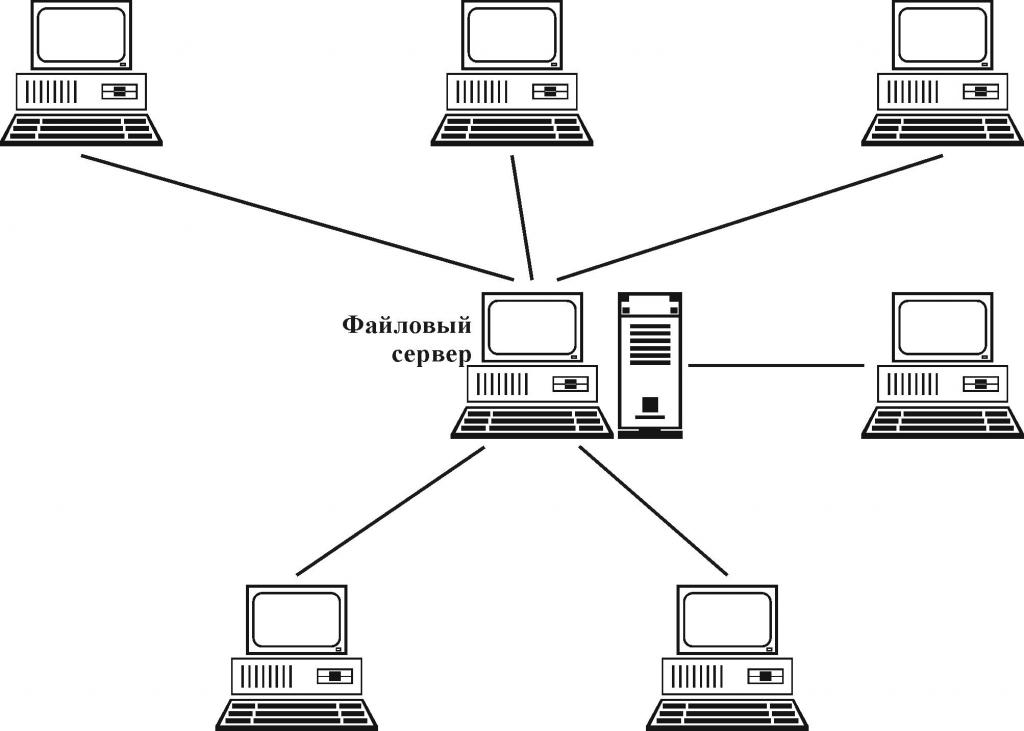
The essence of such a combination of computers into a single whole is that they all connect directly to the central terminal (server) and have no connections with each other. Absolutely all transmitted and received information passes directly through the central node. And it is this configuration that is considered the most secure. Why? Yes, only because the introduction of the same viruses into the network environment can be done either from the central terminal, or accessed through it from another computer device. However, it seems very doubtful that in such a scheme of a local network of an enterprise or a state institution, a high level of central server protection will not be provided. And you can only implement spyware from a separate terminal if you have physical access to it. In addition, quite a serious restriction may be imposed on each network computer from the central node, which can be observed most often when using network operating systems, when computers do not even have hard disks, and all the main components of the operating system used are downloaded directly from the main terminal.
But there are drawbacks. First of all, this is due to increased financial costs for laying cables if the main server is not in the center of the topological structure. In addition, the speed of information processing directly depends on the computing capabilities of the central node, and if it fails, respectively, on all computers included in the network structure, communications are broken.
Bus pattern
The connection scheme in the local network by the type of “bus” is also one of the common ones, and its organization is based on the use of a single cable, through the branches of which all terminals are connected to the network, including the central server.
The main disadvantage of this structure can be called the high cost of laying cables, especially for those cases when the terminals are at a sufficiently large distance from each other. But in the event of failure of one or more computers, communications between all other components in the network environment are not violated. In addition, when using such a local network scheme, the circuit passing through the main channel is often duplicated at different sites, which helps to avoid damage to it or the impossibility of its delivery to the destination. But security in such a structure, alas, suffers quite a lot, because malicious virus codes can penetrate all other machines through a central cable.
Ring structure
In a sense, the ring diagram (topology) of a local area network can be called morally obsolete. To date, it is not used in almost any network structure (except perhaps in mixed types). This is connected precisely with the very principles of combining individual terminals into one organizational structure.
Computers are connected to each other in series and with only one cable (roughly speaking, at the input and output). Of course, this technique reduces material costs, but in the event of failure of at least one network unit, the integrity of the entire structure is violated. If I may say so, in a certain area where a damaged terminal is present, the transmission (transmission) of data is simply stopped. Accordingly, even when dangerous computer threats penetrate the network, they pass in the same sequence from one terminal to another. But in the event of the presence of reliable protection at one of the sites, the virus will be eliminated and will not go further.
Mixed types of networks
As mentioned above, the main types of local area network schemes in their pure form are practically not found. Mixed types, in which elements of the main types of network circuits may appear, are much more reliable both in terms of security, cost, and ease of access.
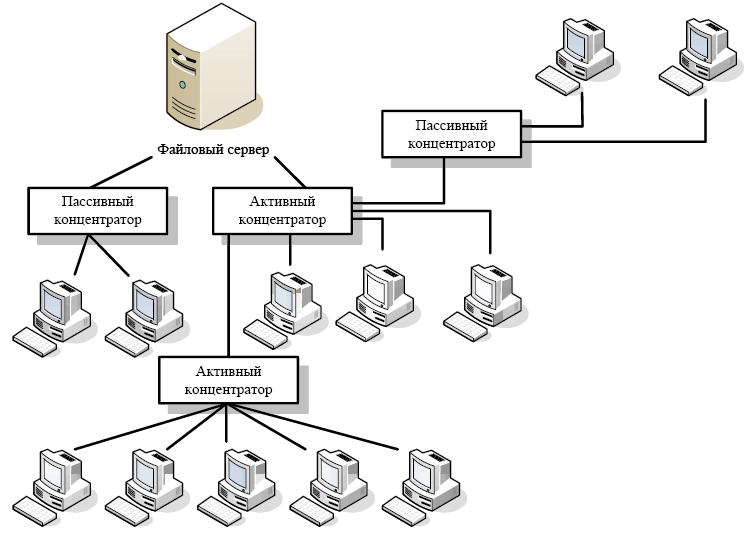
So, very often you can find networks with a tree structure, which initially can be called a kind of “star”, since all branches come from one point, called the root. But the organization of branches in such a local area network connection scheme can contain both ring and bus structures, dividing into additional branches, often defined as subnets. It is clear that such an organization is quite complex, and during its creation it is necessary to use additional technical devices such as network switches or splitters. But, as they say, the end justifies the means, because thanks to such a complex structure, important and confidential information can be protected very reliably by isolating it in the subnet branches and practically restricting access to it. The same applies to the failure of components. With this construction of local area network schemes, it is completely optional to use only one central node. There can be several, with completely different levels of protection and access, which further increases the degree of overall security.
Logistic Topology
When organizing network structures, it is especially important to pay attention to the methods used for data transfer. In computer terminology, such processes are called logistic or logical topology. At the same time, physical methods of transmitting information in various structures can very significantly differ from logical ones. It is logistics, in essence, that determines the transmission / reception routes. It is often seen that when building a network in the form of a “star”, information is exchanged using the bus topology, when the signal can be received simultaneously by all devices. In ring logical structures, one can encounter situations when signals or data are received only by the terminals for which they are intended, despite even sequential passage through all the associated links.
The most famous networks
So far, we have exclusively considered the construction of local area network schemes based on Ethernet technology, which in its simplest terms uses TCP / IP addresses, protocols, and stacks. But in the world you can find a huge number of network structures that have different principles of network organization from the above. The most famous of all (except Ethernet using a logical bus topology) are Token Ring and Arcnet.
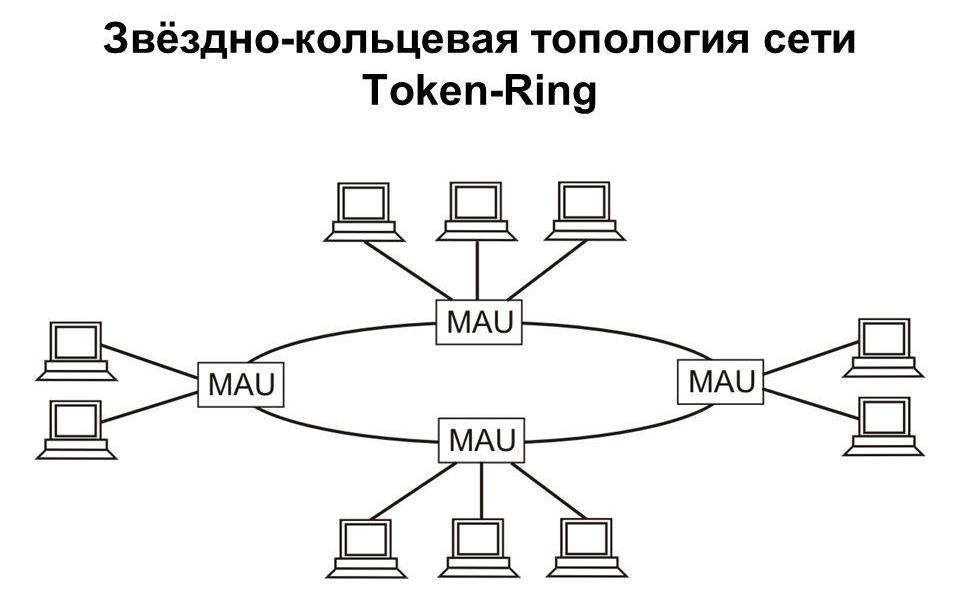
The Token Ring network structure was once developed by the notorious IBM company and is based on the logical circuit of the local network “marker ring”, which determines the access of each terminal to the transmitted information. In physical terms, a ring structure is also used, but it has its own characteristics. For combining computers into a single unit, it is possible to use either twisted pair or fiber optic cable, but the data transfer rate is only 4-16 Mbit / s. But the “star” type marker system allows you to transmit and receive data only to those terminals that have the right to do this (marked with a marker). But the main drawback of such an organization is that at a certain moment only one station may have such rights.
No less interesting is the Arcnet local network diagram created in 1977 by Datapoint, which many experts call the most inexpensive, simple and very flexible structure.
Coaxial or fiber optic cables can be used to transmit information and connect computers, but the possibility of using twisted pair cable is also possible. However, in terms of transmit / receive speed, this structure cannot be called particularly productive, since at the maximum packet exchange can be carried out at a connection speed of no more than 2.5 Mbit / s. As a physical connection, the "star" circuit is used, and in the logical - "marker bus". With the rights to receive / transmit, the situation is exactly the same as with Token Ring, except that the information transmitted from one machine is accessible to absolutely all terminals included in the network environment, and not to any one machine.
Brief information on setting up a wired and wireless connection
Now briefly dwell on some important points in the creation and application of any of the described schemes of the local network. Third-party programs when using any of the well-known operating systems to perform such actions are not needed, since the basic tools are provided in their standard sets initially. However, in any case, it is necessary to take into account some important nuances regarding the configuration of IP addresses, which are used to identify computers in network structures. There are only two varieties - static and dynamic addresses. The former, as the name implies, are constant, and the latter may change with each new connection, but their values are exclusively in the same range as set by the communication service provider (provider).
In wired corporate networks, to ensure a high speed of data exchange between network terminals, static addresses are assigned most often to each machine on the network, and dynamic addresses are usually used when organizing a network with a wireless connection.
To set the specified parameters of the static address in Windows-systems, the IPv4 protocol parameters are used (in the post-Soviet space, the sixth version is not yet widely used).
It is enough to specify the IP address for each machine in the protocol properties, and the parameters of the subnet mask and the main gateway are common (unless a tree structure with many subnets is used), which looks very convenient from the point of view of quick connection setup. Despite this, dynamic addresses can also be used.
They are assigned automatically, for which there is a special item in the TCP / IP protocol settings, at each specific moment in time they are assigned to network machines directly from the central server. The range of addresses allocated is provided by the provider. But this does not mean at all that the addresses are repeated. As you know, in the world there cannot be two identical external IPs, and in this case it is either that they change only within the network or are transferred from one machine to another when some external address turns out to be free.
In the case of wireless networks, when routers or access points that distribute (transmit or amplify) a signal are used for the initial connection, the setup looks even simpler. The main condition for this type of connection is to automatically obtain an internal IP address. Without this, the connection will not work. The only parameter that can be changed is the addresses of the DNS servers. Despite the initial installation of their automatic receipt, it is often (especially when reducing the connection speed) it is recommended to set these parameters manually, using, for example, free combinations distributed by Google, Yandex, etc.
Finally, even if there is only a certain set of external addresses by which any computer or mobile device is identified on the Internet, you can also change them. For this, many special programs are provided. . , VPN-, -, , IP, , , , , ( ). (VPN- ) (, SafeIP), , , -.
Epilogue
, . , , . , () . , , , , , . – , .