Viruses from the very beginning of the creation and development of computer technology have become quite widespread. Some of them were and are completely harmless, the damage from the impact on computer systems from others is estimated at billions of dollars. History knows many examples of the manifestation of viral activity, which led to real epidemics, infecting user PCs and performing their destructive functions. The following is a brief review of the world's most dangerous computer viruses, which at one time had the most significant impact on computer systems around the world.
What is a virus in terms of computer technology?
In general, computer viruses mean not some abstract concept, but the most common software that affects a computer system (in particular, the operating system, applications installed in its environment or user files) with the aim of harming, data theft, extortion payments for decrypting files, etc. Such programs themselves contain special executable codes that are activated either directly upon penetration into the system, or at a certain point in time, but aimed at launch completely different operations. Firstly, the main code is intended for the main action for which the virus itself is designed. Secondly, very often parallel processes are launched that allow viruses to hide from the user's eyes or antivirus software (disguise themselves), working in the background and replacing some system components with their own applets. Thirdly, along the way, they can start operations on self-copying, embedding code in installed programs, sending themselves on the Internet or over the network, etc.
There are a lot of types of virus threats today, and the list of their types by classification looks quite impressive (trojans, worms, ransomware, ransomware, stealth viruses, polymorphic applets, spies, keyloggers, resident or non-resident threats, and many others), not to mention that some types of threats cannot be attributed to any one class. However, if we talk about the most dangerous viruses in the world for a computer, almost all of them are classified as worms. At the dawn of the development of computer technology, they penetrated the system mainly through removable media (floppy disks), but with the advent of the Internet they began to be transmitted by e-mail or settled on various websites on the World Wide Web.
The most dangerous computer viruses in the world
The statement that viruses, as a threat to computers, arose at the time the technology itself appeared in the form of home PCs, looks completely wrong. The fact is that such technologies began to be actively developed in the early 50s of the last century. By 1961, even the Core War movement was even formed among programmers, which was a kind of competition for the inconspicuous destruction of each other's programs. But the official date for the emergence of threats, called computer viruses today, is called 1981, when the Elk Cloner and Virus 1,2,3 viruses were created, the codes of which were designed to run on Apple II computers. Subsequently, the bulk of the threats began to focus mainly on Windows and Linux-systems, although it is believed that Linux and the "apple" OS are more resistant to their effects. The progenitor of all the threats known today is the notorious Brain virus, which made a lot of noise in 1986. At the moment, there are several main threats that are considered to be the most dangerous in the short history of computers, among which the most famous are the following:
- Brain.
- Jerusalem
- Morris Worm.
- Michelangelo.
- CIH (Chernobyl).
- Melissa
- I love you.
- Nimda.
- Code Red.
- SQL Slammer.
- Sobig f
- MyDoom.
- Conficker
- Stormorm
- Petya.
- WannaCry.
Brain
Initially, this software was created by two brothers, programmers from Pakistan, and by its nature it was not a virus. This applet was only to punish users of their own software without a license by removing installed applications from their computers.
But, as it usually happens, the virus got out of control and infected several tens of thousands of computers around the world (18 thousand only in the USA). He replaced bootable infected entries with neutral ones, and therefore attempts to detect it until a certain time were completely futile.
Jerusalem
No less dangerous and harmful was the viral applet, called Jerusalem, which in 1988 received the greatest distribution in Europe, the USA and the Middle East. The essence of its effect was that infected executable files were immediately deleted when they were launched. But the side effect looked much more unpleasant. If the 13th day was on Friday, the virus applet spontaneously started full formatting of the hard drive.
Morris Worm
This virus is called almost one of the most brilliant creations, which was created by a 23-year-old student from the United States in the same 1988.
His action looked twofold. On the one hand, he was able to select passwords for access to operating systems using a dictionary containing only 400 words. On the other hand, it brought computers to a state of complete dysfunction, constantly copying themselves and sending copies via the Internet. Total damage at that time was estimated at about $ 100 million. It is also noteworthy that if Morris had not admitted his authorship of this applet, the creator would never have been found. By the way, in essence this virus can be called the first network worm (it spread via the ARPANET network).
Michelangelo
This virus, by its nature, initially did not pose any danger, because after penetrating computers from floppy disks until a certain point it was inactive and waiting for a convenient moment to attack. That moment was the birthday of Michelangelo - March 6. On this day, the virus was activated in the system and destroyed absolutely all the data stored on the hard drive.
CIH (Chernobyl)
In the same 1988, another applet called CIH, created by a Chinese programmer, was born. The name was formed by the first letters of his name, and behind the scenes the virus was called Chernobyl due to the fact that it became active just on the anniversary of the Chernobyl accident (April 26). It received the greatest distribution in East Asia, however its impact on computers looked already more destructive.
The fact is that he deleted not only information on the hard drive, but also completely erased the BIOS software shell. Infection of approximately 300 thousand computers was officially confirmed, and according to unofficial information, the total number of affected PCs was at least half a million.
Melissa
One of the most dangerous computer viruses in the world is still considered the notorious applet Melissa, which made a lot of noise in 1999.
The virus infected mail servers, looked up email addresses on the user's computers (the first 50 in the address book), and sent out not only its own copy, but also letters with contents that would be classified as spam today. In some ways, the effects of the Melissa virus on mail servers were similar to what are now called DDoS attacks. Thus, their work was completely paralyzed due to overloaded systems, and the total damage amounted to about $ 100 million.
ILoveYou virus
The year 2000 in the computer world added turmoil. It is this time that is associated with the emergence of one of the most harmful viruses, ILoveYou. It has spread worldwide through email.
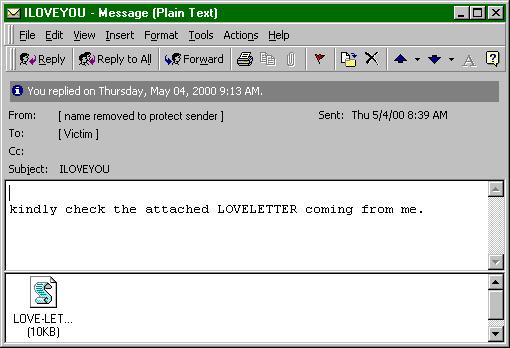
The recipients received a letter with an attachment disguised as a text file with a declaration of love. The subject of the message and the name of the attachment just indicated I Love You. In fact, the contents of the attachment was the most common executable script written in Visual Basic, which, after starting, not only destroyed files on the hard disk or in a networked environment, but sent out copies of it to all contacts from the address book. The creators of the applet I Love You turned out to be very resourceful and played on human weaknesses (who is not interested, who declares your love?). Experts estimated the total damage from infection at about 10-15 billion dollars. By the way, by the scale of spread and infection, the virus was included in the Guinness Book of Records as the most dangerous threat to modern times.
Nimda is another virus
The multi-vector worm Nimda (the name is the word Admin, written in reverse), the world saw in 2001. He used several basic methods of distribution on the network and on the Internet, as a result of which he hit millions of terminals in just 22 minutes. At that time, he was considered the most famous Internet worm.
Code red
Another virus that has made noise in the world is called the “red code”. It entered computers through browsers associated with the Microsoft IIS web server.
Its effect was reduced to replacing system components with its own infected files, and after its activation in the computer system, the line “Hacked by the Chinese!” Appeared on the monitor screen. with an invitation to visit worm.com. It is noteworthy that the virus even infected White House computers, and was created by ethnic Chinese from the Philippines.
Slammer
SQL Slammer is a worm that hit Microsoft's servers in 2003, as well as another 500,000 servers worldwide.
Due to the high speed of distribution and the impact of the type of DDoS applets, it literally in a matter of minutes significantly reduced the bandwidth of the servers, and South Korea was completely isolated from the Internet for as much as 12 hours. It took a record short time to defeat - in just 10 minutes, about 75 thousand computers were infected!
Sobig f
Sobig F virus in 2003 set a kind of record for infection. About a million computers were exposed to it.
Like the notorious "love" applet, it was distributed through email attachments, and Microsoft even set a reward of $ 250 thousand for providing at least some information about its creators, which have not yet been installed. As a result of the impact, the damage was estimated at 10 billion dollars.
MyDoom
MyDoom virus in 2004 is almost a complete analogue of the previous threat, but broke its record in terms of speed of distribution and the number of infected systems.
Its impact mainly affected Windows computers and boiled down to the fact that users could not access anti-virus application sites, open news feeds, or even access some sections of Microsoft’s official Internet resources.
Conficker
A real storm in the form of enhanced DDoS attacks struck in 2009, when the Conficker virus appeared. A description of its effects is as follows. After penetrating both computers and even smartphones, the applet, as it were, united their computing capabilities into a single whole, after which it attacked the selected resources. The damage from its impact is almost expressed in an astronomical sum - 9.1 trillion dollars!
Stormorm
This viral applet is considered to be a kind of botnet designed for DDoS attacks. The time of its appearance dates back to 2007, and as the creators are often called programmers, presumably with Russian roots. According to preliminary estimates, about a million computers worldwide were infected, and it was obviously created by professionals who used the most advanced computer and network technologies at that time.
Petya
This applet is one of the most recent, and the time of its appearance dates back to 2016. Its first modifications merely blocked access to data on computers by encrypting files, when a certain amount was required to pay for decryption. In other words, this applet simultaneously became both a cryptographer and a ransomware. However, the latest versions of the virus have also "learned" to hit the boot records of the Windows operating systems themselves. It is believed that these were only trial attacks, and a real full-scale impact should be expected in the near future.
Wannacry
Finally, this virus looks very similar to the previous threat, however, it only requires cryptocurrency (bitcoins) as payment, operations with which are almost impossible to track in most known financial settlement systems.