The very concept of activator has a lot of meanings. However, in the case of software used on any computer, the interpretation of this term is significantly narrowed. It is further proposed to consider what an activator is, what types of such software exist, how to use such programs, and how appropriate or even legal it is to use some of them. Let us dwell separately on computer security issues and the risks associated with the use of applications of this type.
What is an activator in a general sense?
In general, based on the definition itself, it is customary to call an activator a program capable of generating certain code that needs to be used for an operating system or some installed software product in its environment in order to be able to use more complete functionality, for example, in the case of installing trial versions BY. Sometimes you need to activate a product immediately after installation, because an installed program without entering a special key can be completely inoperative. But why then do you need activators if you can simply enter the desired license code? The whole problem is that such licenses usually need to be bought. And that is why almost all well-known programs for generating codes and keys can conditionally be attributed to illegal software. In some cases, however, in order for the program to work, it is enough to simply register on the developer's site or in some special service. But this is very rare.
Types and purpose of activators
Now a few words about what an activator is in terms of ensuring the operability of a particular software product.
It's no secret that even operating systems behave rather capriciously, without timely entering the license code, losing some of their capabilities that are blocked, constantly rebooting at the most inopportune moment, etc. How does the activator work in this sense? Here you need to make the difference between external and internal activators. External ones simply generate codes, which are then used to activate the OS or applications, but internal ones usually check such combinations with their databases (usually so that the same software product, if it is not provided by the developer, is not used on several computers simultaneously , or the authenticity of the entered key was confirmed). Thus, it becomes clear that an external code-generating program is completely useless if there is no built-in activator in the activated application.
Activators for operating systems
What does “activator” mean in a general sense, a little understood. Now let us dwell on a few typical examples characteristic of modern software products. First of all, we will consider the basic methods of activating Windows operating systems. Regrettably, users of computers operating under their control in the post-Soviet space are in no hurry to lay out money for their official purchase, preferring to use proven pirated methods. So, for example, activators of the maximum modification of Windows 7 or any other paid version of the operating system can be performed through the use of specialized unofficial utilities. You can find a lot of them. However, reviews of the KMSAuto Net activator indicate that this particular portable application is one of the most popular.
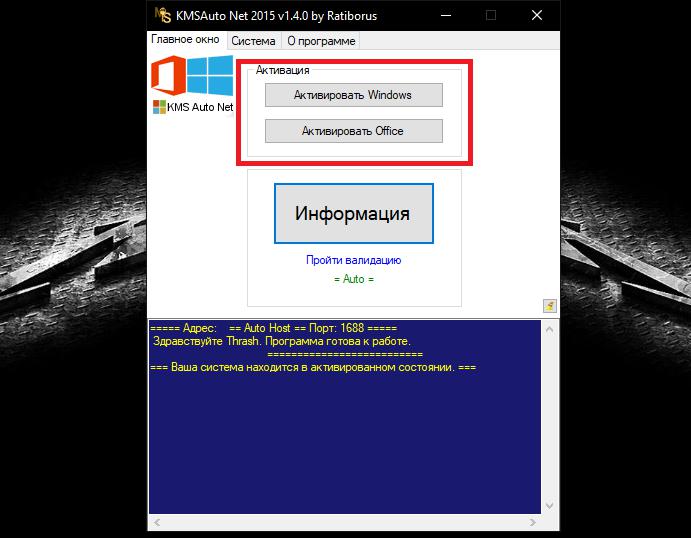
This is due to the fact that the program not only generates special code, but also embeds it in the OS shell without user intervention. At the same time, the utility, as an additional measure, uses the creation of a special periodically performed task in the “Task Scheduler” of the system and performs repeated “reactivation” every ten days. As already clear, you cannot delete the application file from the computer, because after a certain period the operating system will simply stop working.
Office Product Applications
A significant advantage of such utilities is the fact that many applications are able to generate keys not only for the OS itself, but also for office suites from Microsoft, regardless of the year of release.
Such capabilities are available in KMSAuto Net, and in KMSpico, and many others. To activate the "Office" (which is also a paid software package), just click the appropriate button, after which the same operations will be performed as for the operating systems.
Official activation of antiviruses
In the case of antivirus software, such utilities do not work. Since almost all such software products have built-in self-defense tools, the use of external programs is not provided (when they try to intervene in the internal structure of the antivirus, they will simply be marked as threats and isolated). But how to get around such restrictions? There are a lot of opinions on this subject, however, most experts recommend using shareware official software products, but with the condition of their activation every thirty days (or for a longer period). You can use freely laid out keys. But this is not an option. And here special “rectifiers” of licenses come to the rescue, as, for example, it is provided for for ESET protective equipment.
On the official website on the Internet you can enter a username and password, after which a license will be generated, which is inserted into a special field of the internal activator of the antivirus. Note that there is nothing illegal here.
Other type of program activators
It should be noted separately that such utilities can be found for many paid programs (for example, the same key generators). If you define what an automated type activator is, the easiest way to explain this is with the example of actions with software products from Native Instruments.
You can use a universal activator for them, which generates and inserts licenses for absolutely all the programs of this developer installed in the system. For some other applications, activators intended only for them are used. But alas, such actions are, to put it mildly, illegal.
Other types of license bypass
As for other types of activation, one can often come across some hacker methods that involve replacing the original program files with cracked ones by manual copying or using tools like Symlink Installer (usually EXE and DLL formats), inserting illegal license files with the associated installation of prohibitions on checking the authenticity of the codes by restricting the Internet access program (most often through the hosts file), etc.
The most advanced activator creators went even further, managing to offer users special REG files, after merging the contents of which with the system registry, special keys and entries are installed, by which the program sees supposedly legitimate activation even after checking its own key database.
Security questions
Most unofficial activators have their own certificates of authenticity, security and even digital signatures, so at an early stage antiviruses may not respond to such programs at all. But portable scanners easily identify activators as unwanted software, and many of them neutralize them, allegedly referring to the fact that they contain virus threats (Trojans are most often detected). Thus, before applying illegal methods of activation of any type of software, the user must first weigh the pros and cons, and only then decide on how appropriate it is to use activators in each case.